In this blog post we will cover:
- Why create cybersecurity risk thresholds?
- Definitions
- Top Down vs. Bottom Up
- Safe Security’s Approach
- Examples:
- Escalate Cyber Risk to Appropriate Decision-Making Bodies
- Establish a Risk Treatment Plan and Justify Investment Decisions
- Proactively Determine Pre-Incident Materiality Thresholds
- Conclusion
Why create cybersecurity risk thresholds?
There are many reasons to create cybersecurity risk thresholds. The Securities and Exchange Commission’s (SEC) Cybersecurity Disclosure rule has increased awareness of the need for public companies to measure materiality of cyber risk. Later in this blog post, we will further discuss how creating risk thresholds is beneficial to complying with the SEC’s ruling.
Ultimately, the reason organizations should create cybersecurity risk thresholds is:
to operationalize the decision-making process for cybersecurity risk
While companies may have other reasons for creating risk thresholds, the most significant benefit to the organization is improving the decision-making process and making it actionable. Operationalizing the decision-making process includes making it explicit and creating objective criteria for:
- reporting and escalation to decision-making bodies (e.g., Cybersecurity Risk Steering Committee)
- organizational alignment on risk treatment (accept/mitigate/transfer)
- proactively measuring likelihood and magnitude of potential loss events to establish materiality thresholds before an incident occurs
Definitions:
The terms risk appetite, risk threshold, and risk tolerance are often used interchangeably. However, there are a few important distinctions that differentiate between the terms.
- Risk Appetite: The amount of risk an organization is willing to accept.
- Risk Threshold: The point (either likelihood [%] or magnitude [$]) at which an organization deems it must take a specific action.
- Risk Tolerance: The acceptable deviation from an organization’s Risk Appetite.
We will intentionally use the term Risk Threshold throughout this post to describe the process of identifying decision points using quantitative cyber risk metrics.
Note: For the sake of simplicity, we use “Risk Tolerance” in the SAFE One platform to cover all these terms.
Top Down vs. Bottom Up:
Cybersecurity risk thresholds and materiality should be a “top down” directive agreed upon by Legal, Finance, IT, Enterprise Risk Management, and ultimately owned by Senior Leadership, and the Board (the specific parties involved in establishing risk thresholds may differ per organization).
The problem with assuming a “top down” approach is that the groups listed above typically do not possess quantitative cyber risk metrics (such as likelihood and magnitude) or the expertise to establish cyber risk thresholds. In other words, Senior Leadership and the Board of Directors most likely do not (and should not be expected to) know the probable likelihood and magnitude of cyber loss events that can be used to establish cyber risk thresholds.
As cybersecurity risk programs mature, the cyber risk function within an organization has the responsibility to proactively propose risk thresholds (in a “bottom up” manner) that can be reviewed, approved, challenged, and iterated upon through feedback from Senior Leadership and the Board.
Leadership and the Board are not required to be subject matter experts in cyber risk. Leadership and the Board should, however, be able to validate cyber risk thresholds in the context of business risk. The cybersecurity risk program must provide relevant data to leadership and the board to communicate cyber risk in financial terms [(loss magnitude ($) and likelihood (%)].
LEARN MORE: How to Improve Cyber Risk Communication to the Board and Senior Management
FAQ: Loss magnitude/likelihood vs. Annualized Loss Exposure (ALE)
Q:
- Why should we focus on loss magnitude and likelihood as individual factors rather than use one number such as Annualized Loss Exposure (ALE)?
A:
- ALE is a useful number for comparing a list of different risk scenarios. However, it is important to remember that while ALE is represented as a single number, it is truly a combination of two numbers (likelihood and magnitude). Combining those two numbers together makes it more difficult to describe the effect of risk treatment options on risk.
- For example, It is difficult to describe how implementing multi-factor authentication (MFA) will impact ALE. It is less difficult to describe how implementing MFA will reduce the likelihood of an external actor gaining access to privileged accounts which, in turn, will reduce the likelihood of a data breach caused by an external actor..
- We believe it is both more effective and more realistic to focus on the individual components that can be influenced to reduce risk (either likelihood or magnitude).
Safe Security’s Approach:
- Identify, (quantitatively) assess, and report top cyber risks
- Define thresholds for unacceptable loss magnitude and event likelihood
- Validate thresholds against top cyber risk scenarios
- Adjust thresholds as needed based on feedback from leadership
LEARN MORE about SAFE One, the only AI-driven platform to manage your first-party and third-party cyber risk, enabling your business to safely go faster.
Step 1 - Baseline Top Risks:
The first step in establishing risk thresholds is identifying, quantitatively assessing, and reporting top cyber risks. The top risk “baseline” serves an important purpose. It gives the audience a starting point which they (likely) never had in the past: cyber risk likelihood (%) and magnitude ($).
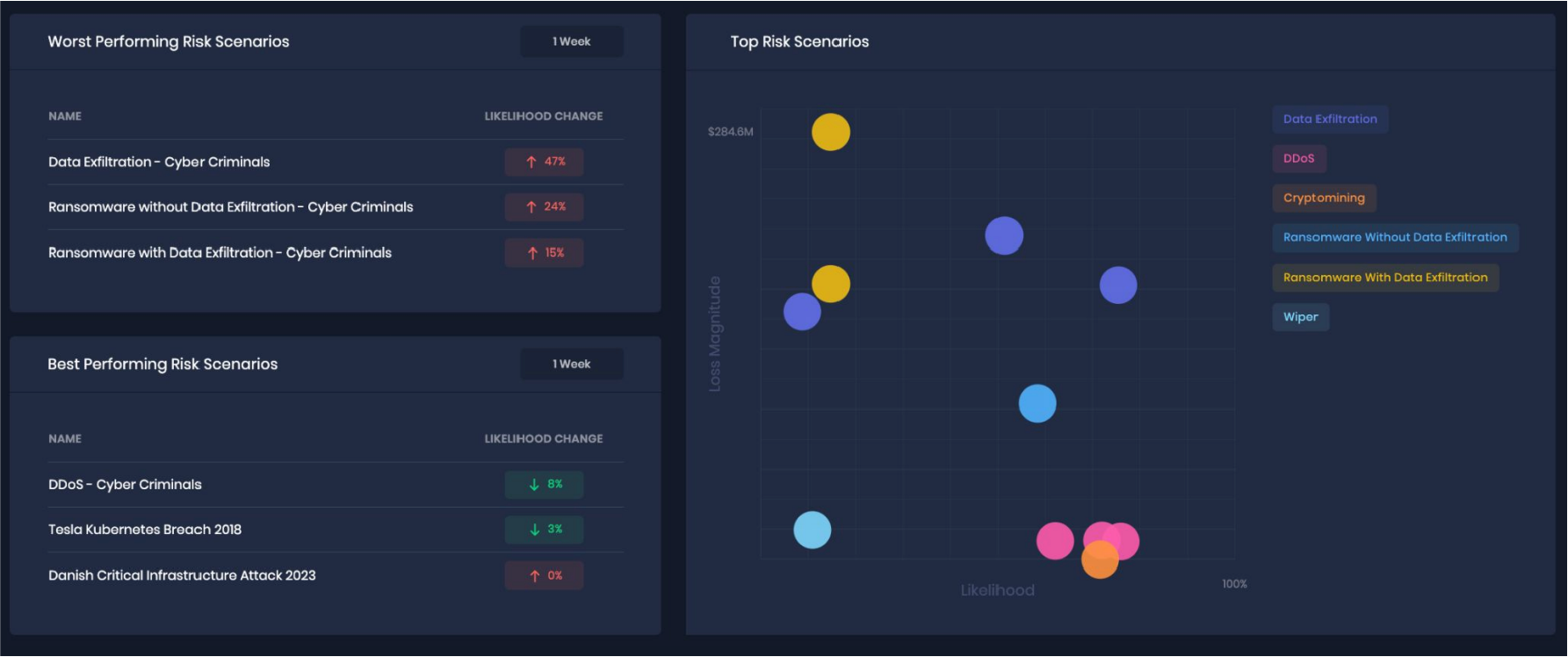
Top Risk Scenarios in SAFE One
Step 2 - Define Thresholds:
Once you have identified and assessed top risks, an effective way to experiment with risk thresholds is to identify gaps in likelihood and magnitude across different risk scenarios. Identifying gaps may help identify abnormal (usually high) risks. For example, if the majority of risks are below $10M per event loss magnitude and 10% annual likelihood, a risk scenario of $40M loss magnitude or 30% likelihood will stand out. You can use the concentration of risk scenarios to “draw a line (or box) in the sand” to start validating risk thresholds.
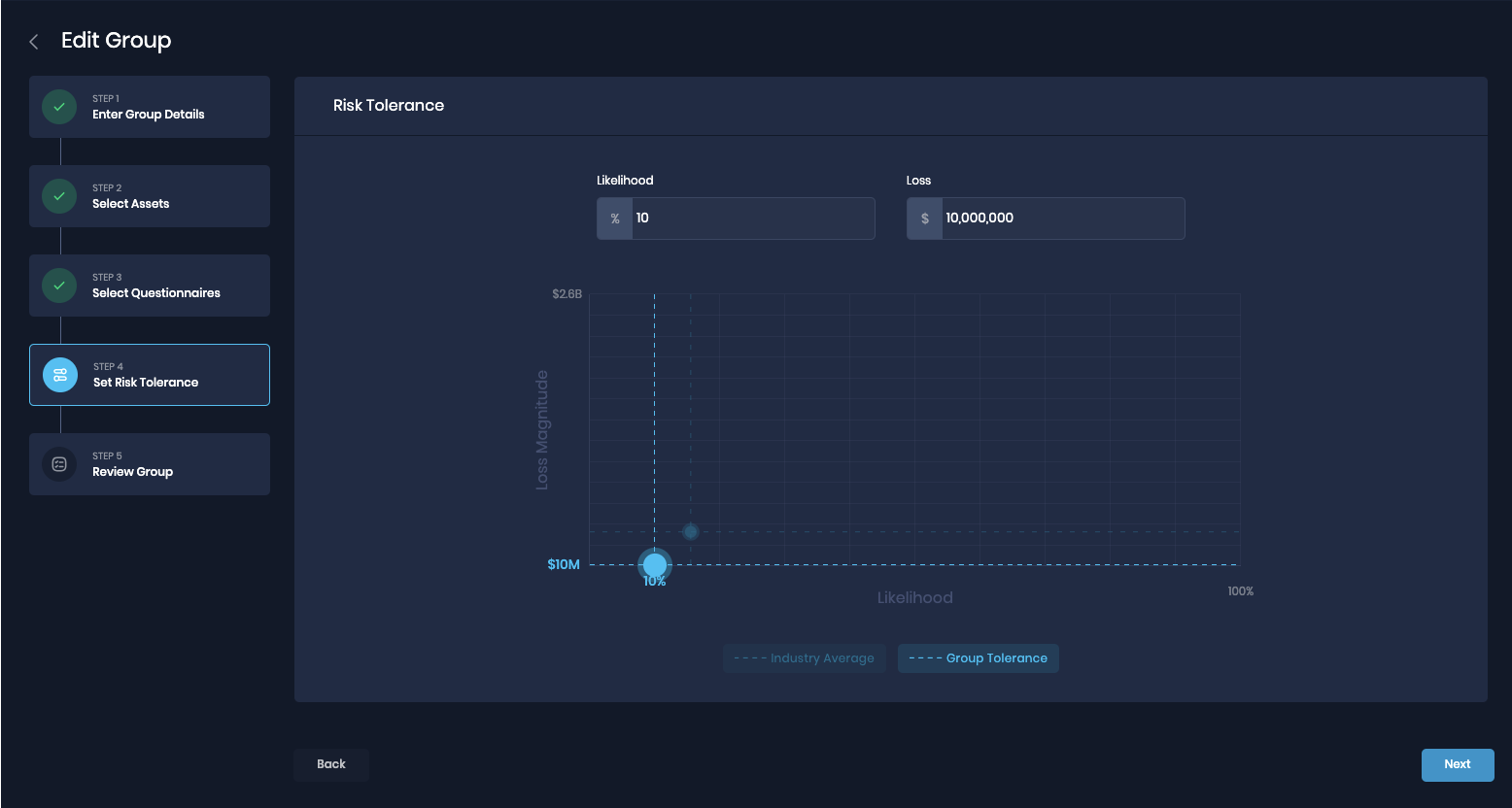
Define Risk Thresholds within Groups in SAFE One
Note: For the sake of simplicity, the SAFE One platform uses “Risk Tolerance” as an umbrella term.
Step 3 - Validate Thresholds:
Once you have defined risk thresholds, socialize them with relevant decision-makers within the organization. Use relevant risk scenarios where possible to give examples. Decision-making bodies such as a Cyber Risk Steering Committee are extremely useful in validating thresholds (see example 1).
Step 4 - Adjust Thresholds:
Adjust thresholds in SAFE One based on feedback from relevant decision-makers. Establish thresholds at the enterprise level first, then consider different thresholds for different areas of the business (Groups in SAFE One).
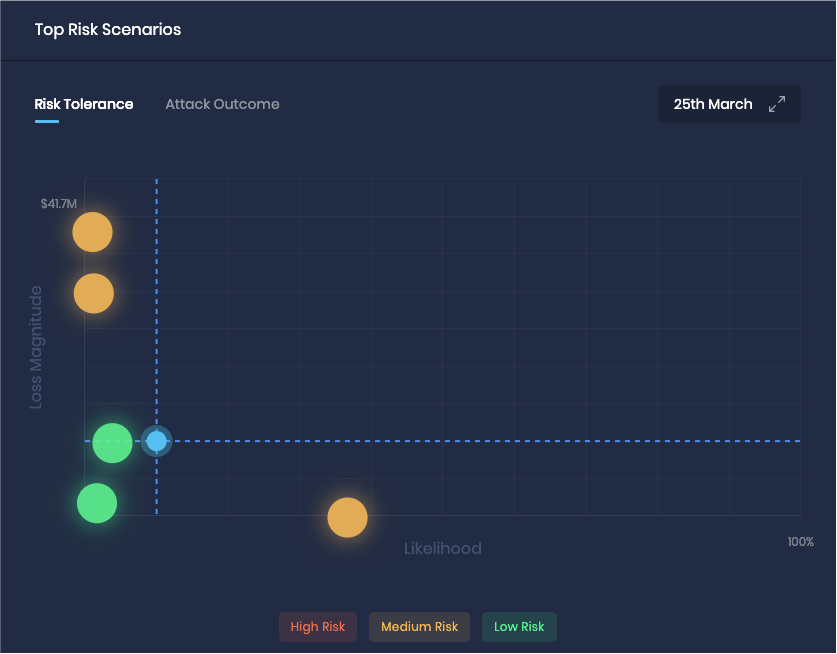
Risk Thresholds applied to Top Risk Scenarios in SAFE One
Example 1: Establish cyber risk thresholds to operationalize escalation to decision-makers
Once you have established initial risk thresholds, socialize them with the relevant decision-making bodies within the organization. Use relevant risk scenarios where possible to give examples.
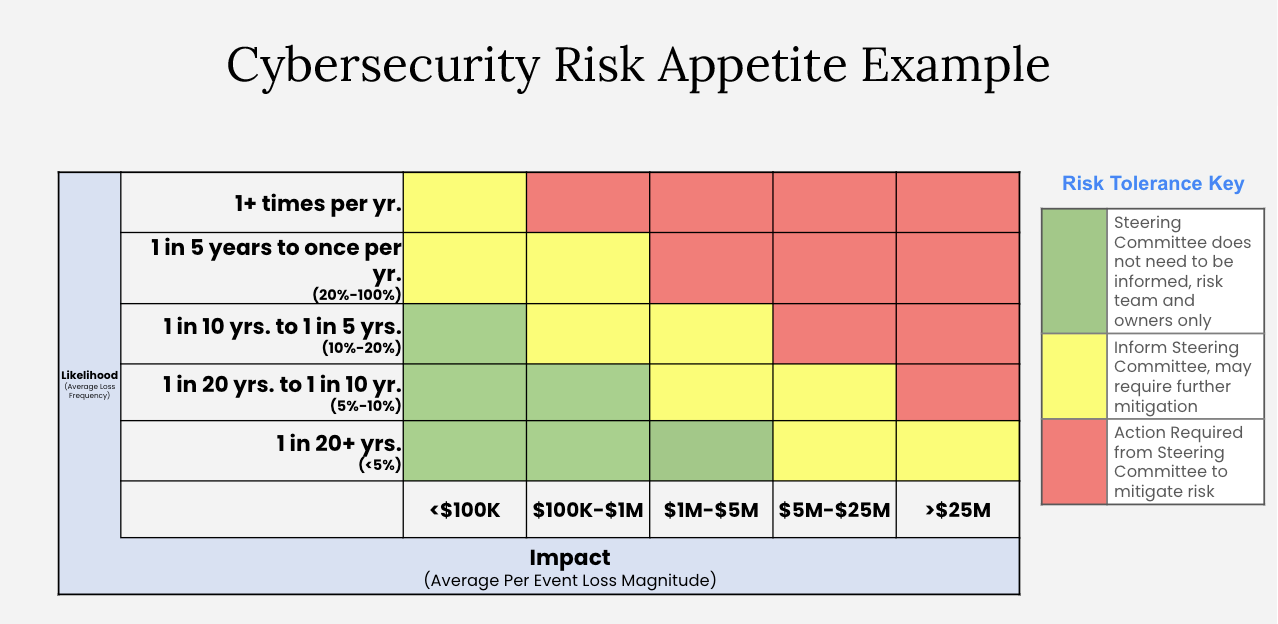
Example Escalation Matrix (5x5)
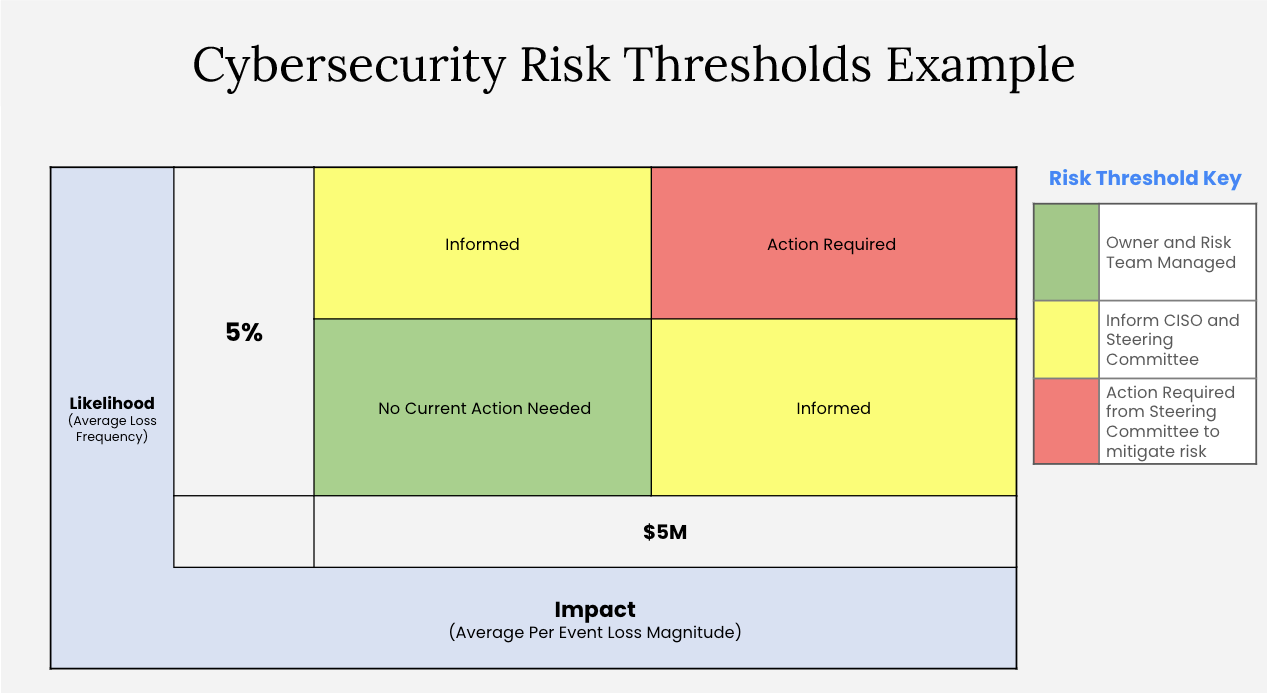
Example Escalation Matrix (2x2)
Example 2: Establish cyber risk thresholds to align on risk treatment and justify investment in controls using SAFE One
Use established cyber risk thresholds to govern the risk treatment workflow within your organization. One potential outcome of using risk thresholds in the risk treatment process is the ability to justify (or turn down) investment decisions.
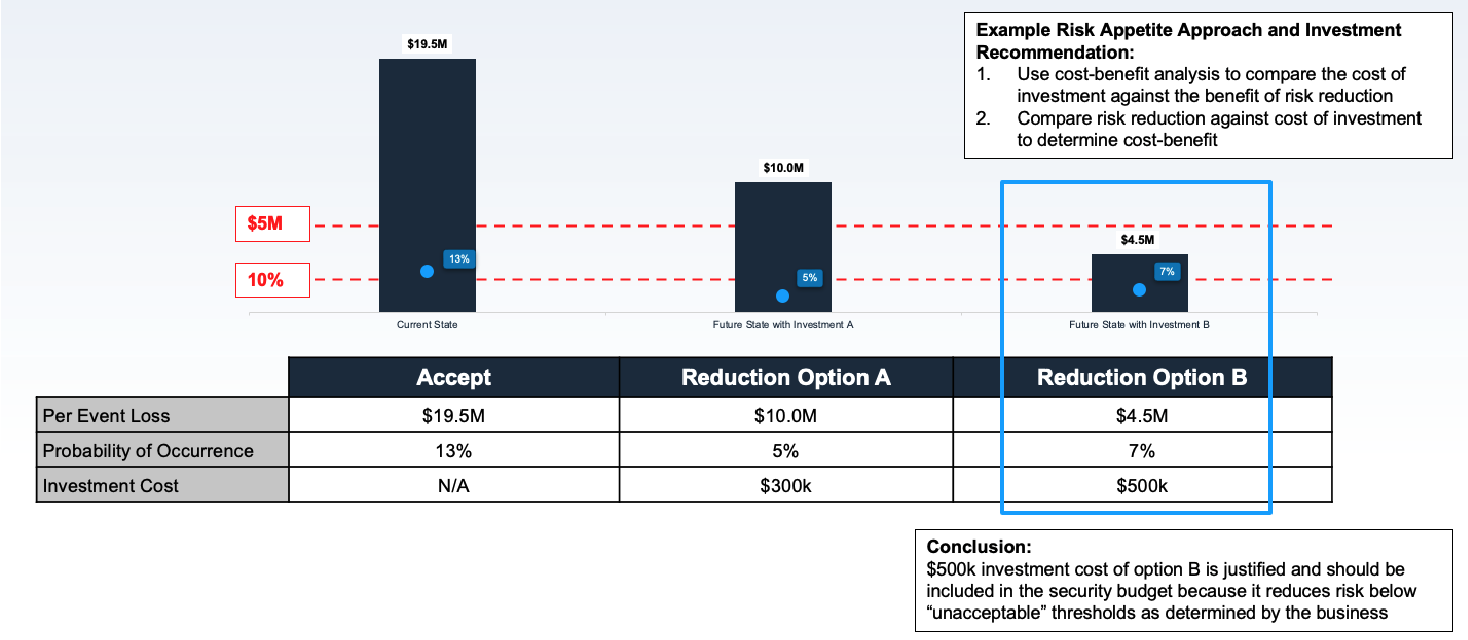
Example Cost-Benefit Analysis
For example, “for any risk above 10% likelihood and $5M magnitude we must explore investment options to reduce the risk below 10% likelihood.
A few things to consider in the risk treatment process:
- The cost of investment should not exceed the benefit of risk reduction
- If investment cost is greater than risk reduction, this could mean:
- Thresholds should be re-evaluated
- Alternative control options should be considered
- How can you measure the cost of control investments?
- Technology cost (the tool being implemented)
- Labor cost (costs to implement the tool)
- Opportunity cost (‘hidden’ cost to the business as a result of implementation) - in other words, does implementing the control conflict with broader business objectives?
Example 3: Proactively measure loss events to establish materiality thresholds before a loss event occurs
If you have already established baseline top risks and defined thresholds, you have the information you need to proactively establish materiality thresholds.
For example, let’s say your loss magnitude threshold is $10M. Depending on the nature of your business, you might determine that the maximum loss your business would experience from any DDoS scenario is $2M. Therefore, if a DDoS event occurs, you should be able to say with confidence that an 8-K disclosure is not required.
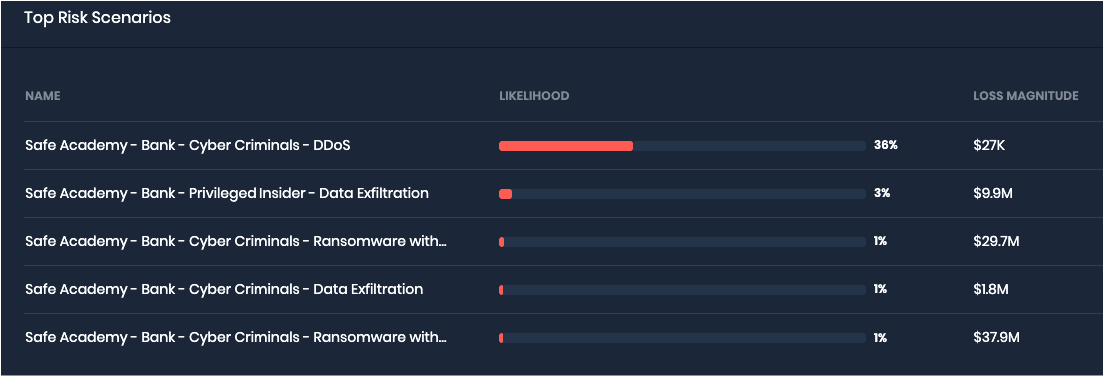
Loss Magnitude from DDoS might never reach a materiality threshold
Loss Magnitude from ransomware might be significantly different depending on factors such as data exfiltration and length of outage.
On the other hand, you might determine that ransomware may or may not exceed the threshold depending on different factors such as:
- How long is the outage? (i.e. “Any outage of ‘business process A’ longer than 7 days will result in revenue loss which exceeds thresholds.” If the outage is shorter than 7 days, 8-K disclosure might be unnecessary.)
- Is there a breach of sensitive data? (i.e. If yes, it is likely to exceed the threshold. If no, 8-K disclosure might be unnecessary.)
These factors can help determine whether a ransomware event would exceed the materiality threshold and whether an 8-K disclosure would be required. Of course, these are simplified examples and other variables must be considered when making a determination on 8-K disclosure.
The only way to build accurate 8-Ks is to proactively estimate materiality
- Identify Top Cyber Risk Scenarios
- Quantify potential materiality of these risk scenarios using FAIR-MAM and SAFE One
- Define ‘materiality thresholds’ for the organization
- Assess effectiveness of post-incident response controls
- Agree on all of the above with stakeholders: GC, Finance, Cyber, IT, Board
LEARN MORE: CISOs Playbook for SEC Compliance
Recent loss events have proven that cyber 8-Ks can impact stock prices. When organizations such as MGM, Caesars, and Clorox declared an event is material OR that they didn’t know whether it was material or not, they experienced a >10% drop in stock price.
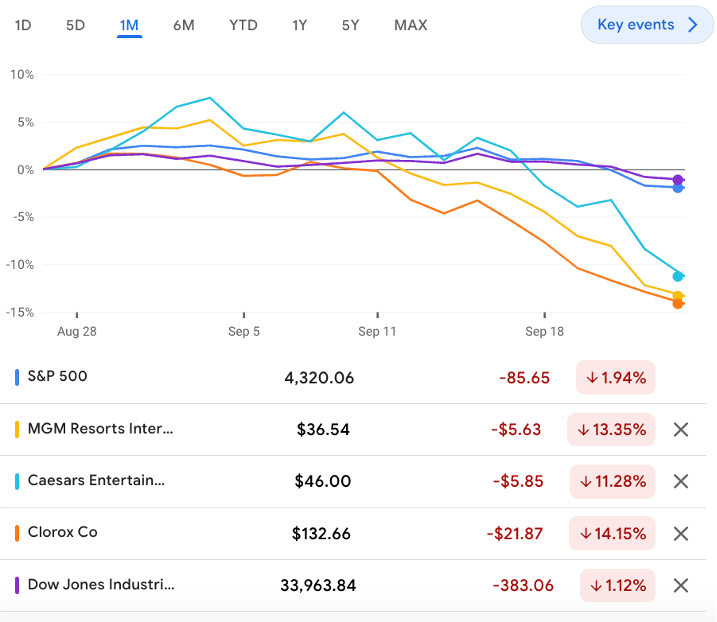
Cybersecurity 8-Ks can have a significant impact on stock price
Most historical cyber events are not material. A company should be able to confidently say that an event is not material. The only way to build accurate cyber 8-Ks is to proactively estimate materiality. Defining materiality thresholds is the first step in that process.
Conclusion:
The most important reason organizations should create cybersecurity risk thresholds is to make the decision-making process for cybersecurity risk explicit and to operationalize it.
Cyber risk quantification (CRQ) is a key maturity step for cyber risk programs, but CRQ for the sake of CRQ is not the end goal. The cyber risk metrics that a program produces should be used to drive better decision-making and shift the mindset from just quantifying risk to actually managing risk.
In this blog post, we described three ways to improve decision-making in cyber risk management using quantitative metrics. Use these examples to operationalize cyber risk decision-making within your own organization.
Contact Us to learn how Safe Security can operationalize better decision-making at your organization.