Ransomware attacks on the healthcare system are surging; attackers have discovered that many healthcare providers are easy marks, poorly defended, and willing to pay ransom rather than risk patient care. Healthcare is also a highly interconnected sector that runs on electronic medical records and payment systems with many single points of potential failure, making fat targets for digital disruption. UnitedHealth Group, the giant in health insurance, exactly fit that profile, setting the stage for the recent hack of its Change Healthcare subsidiary, the worst cyber attack in the history of the US healthcare industry.
Healthcare Under Siege, Providers Reach Breaking Point
Change Healthcare is the dominant clearinghouse for medical insurance claims and payments in the US, accounting for more than one-third of all US healthcare expenditures because of its relationship with 2,400 commercial and government payers. The ransomware attack in February 2024 interrupted all services at Change Healthcare for ten days, and weeks later, payments were still not back at full speed, driving many healthcare providers close to the financial breaking point. Additionally, the attackers breached the personal health information of “a substantial proportion of people in America,” UnitedHealth said in a statement.
According to UnitedHealth disclosures, the cyberattack cost nearly $870 million in Q1 2024, including nearly $600 million in incident response costs and the balance for business interruption. The company estimated that full-year costs will range between $1.4 and $1.6 billion.
That may be an underestimate by the company. An analysis of the hack by Safe Security, using the FAIR Materiality Assessment Model (FAIR-MAM), found that the financial impact to the company could eventually run at twice the level of the company's full-year estimate.

The FAIR-MAM model assesses material risk from cyber events and estimates loss exposure, giving a wider and more accurate cost projection by revealing hidden costs that come due over time. FAIR-MAM was developed by Safe Security in conjunction with the FAIR Institute, the standards-setting industry body for quantitative measurement of cyber risk.
Gathering data from public sources and Safe's own extensive data sets, we are also able to make accurate estimates of losses from data breaches in the news, such as the UnitedHealth hack. The findings are published on the website How Material Is That Hack.
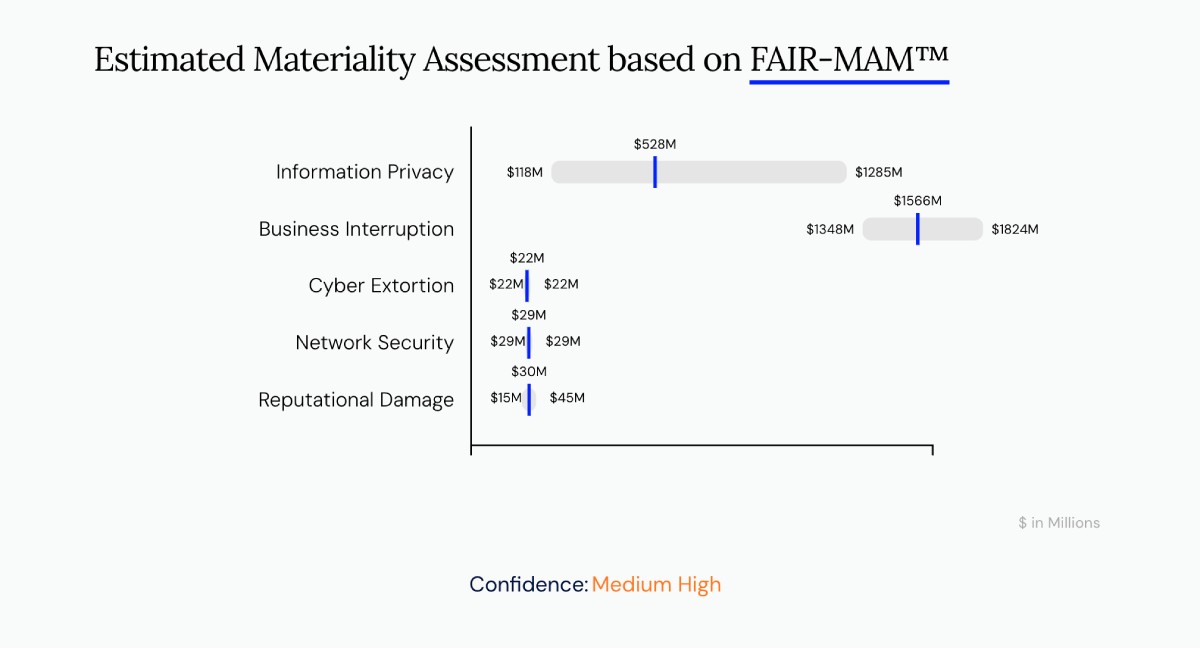
FAIR-MAM analysis decomposes the costs of a cyber event (with over 10 Macro and over 200 Micro Cost Drivers) that come due over time - and, if undisclosed, can lead to sharp scrutiny from regulators and investors. For a healthcare provider or payer, those lurking hazards could include total support over time for customers swept up in a breach of personal health records or class action lawsuit settlements and fines from Health and Human Services, Federal Trade Commission, or other regulators.
Surfacing those hazards is just the tip of the iceberg. The overarching takeaway of the UnitedHealth hack is to step back and reevaluate your core approach to cyber risk management. You need a comprehensive methodology based on an accepted, defensible standard for risk assessment, like FAIR, for assessing cyber risk in financial terms. FAIR-MAM can be an effective first step. The SAFE One platform from Safe Security offers easy, organic implementation of FAIR-MAM and other leading-edge standards to understand and communicate cyber risk management to business decision-makers.
Learn How Safe Security Transforms Your Cyber Risk Management Practice
Proactively Safeguard Shareholder Value with Cyber Risk Management
Above all, the UnitedHealth saga reinforces the urgency for corporate leaders to understand the business consequences of cyber risk. Safe Security, the leader in Cyber Risk Management, enables organizations to adopt a robust cyber risk management framework, process, and tools - so they can be empowered to proactively safeguard shareholder value.
Safe's Fundamentally New Approach - Cyber Risk in Business Terms
Safe empowers the largest global enterprises, including Facebook, Netflix, ADP, Chevron, GSK, Novartis, IHG, and Expedia, along their cyber risk journey with a fundamentally new approach that enables organizations to understand and communicate cyber risk from a business impact perspective. It provides defensible answers to two simple questions: What are my top cyber risks, and what can I do to reduce it? Safe's clear financial articulation of risk allows the board and the business to participate in decision-making and help achieve the right balance between risk reduction and revenue generation.
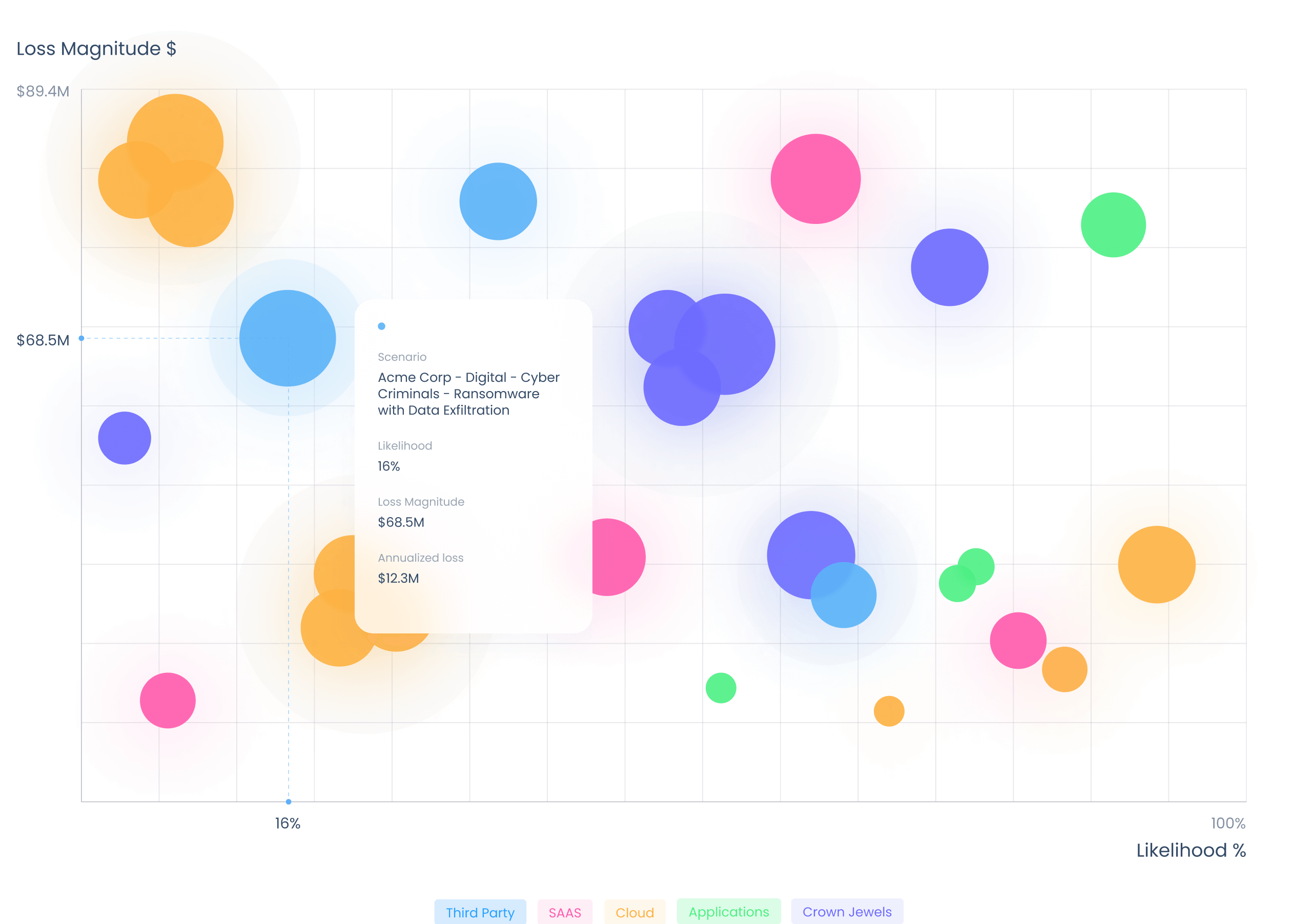
Safe's Complete First and Third-Party Cyber Risk Visibility
Safe delivers the industry's only data-driven, unified platform for managing all of your first-party and third-party cyber risks in real-time. It provides complete cyber risk visibility by automatically ingesting diverse telemetry from 100+ integrations, including CrowdStrike, WIZ, Tenable, Google Cloud, and Amazon.
With Safe X, CISOs can instantly get real-time answers to their most pressing cyber risk questions, such as: What are my top risks? What's changed in my environment? How do I compare to my industry peers? How vulnerable am I to the latest hack?

Prioritized Actions
With Safe's data-driven approach, organizations can confidently prioritize security initiatives/controls according to their business impact. It is the first and only solution to implement the FAIR-CAM model to automate and translate control effectiveness to risk and give you an impact in financial terms. With SAFE One, CISOs can simulate the cost and results of security spending to predict risk reduction, whether it's new solutions, tool expansion, or technology adjustments.

Defensible Output Simplifies Board and Regulatory Reporting & Disclosures
Organizations use the Safe Materiality Assessment Module to quantify the probable frequency and potential loss magnitude of cyber events. This data equips leaders to tune their cybersecurity strategy, prioritize critical gaps, and reduce business risk exposure from cyber events. Users of the Safe Materiality Assessment Module can quickly determine if a cyber incident will have a material impact.
The recent UnitedHealth Group hack underscores the need to move to a robust and defensible cyber risk management practice. It enables enterprises to understand the most critical cyber risks that have the greatest financial impact on the business and prioritize mitigation accordingly. This fundamental shift in cyber risk management equips CISOs to effectively communicate risk trade-offs to the board, stakeholders, and regulators.
To learn more, contact us and schedule a demo today.